10/25/2013
CryptoLocker is such an evil virus that I wanted to create this resource of useful information and links.
Cryptolocker is an extremely dangerous and virulent ransomware trojan. The virus encrypts local and network share drives and then demands either $100 or $300 ransom and gives the user 72 hours to pay.
If you see this on your screen, it is already too late. Your files are encrypted and unrecoverable. Your only hope is a good backup.
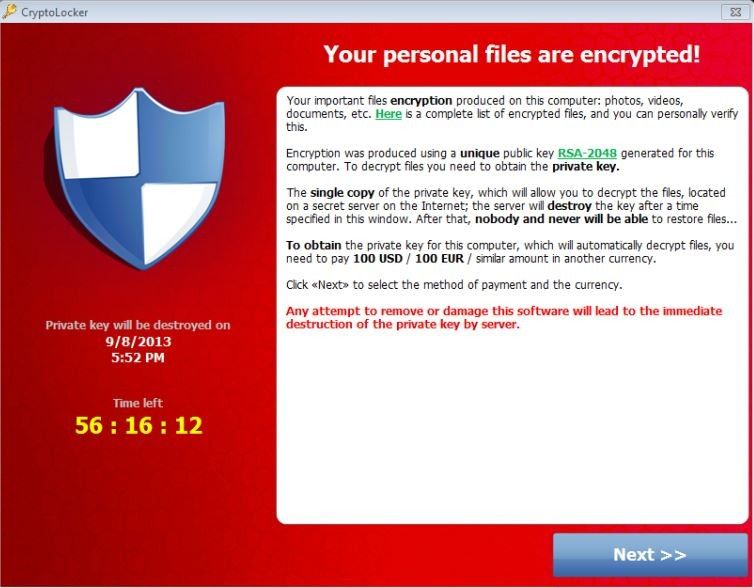
If you read the text, they are correct that "nobody and never will be able to restore files...". The decryption key is stored on their server and you can only get it if you pay the ransom. The clock starts ticking after the files are encrypted. The decryption key will be provided if you pay the ransom and it mostly works, but there are snags that can cause problems, like deleting the list of encrypted files that it uses to decrypt, or deleting their "decrypted file" list in a panic thinking that will help. It only makes it impossible to decrypt them. I think this file is very useful to see the extent of the damage and to find older versions on your backup drive.
Here is the "wonderful" screen that lets you put in Bitcoins or MoneyPak, both unusual payment methods in the U.S. but preferred by the ransomware crowd for anonymity.
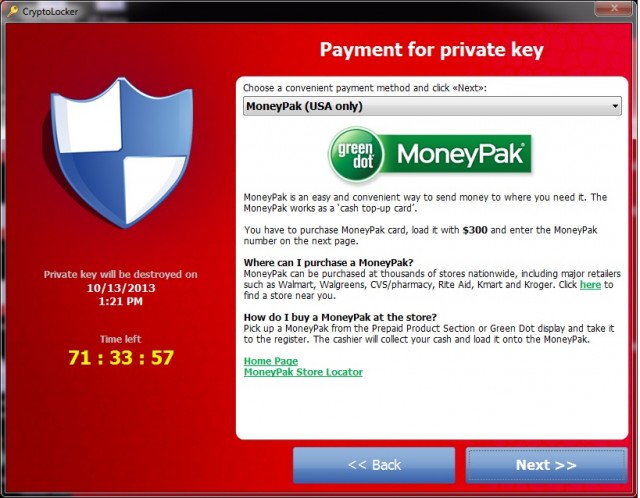
Everyone says "don't pay the ransom" and they are right. (Backup your system now!). But, if you are desperate, and the 72 hour time period has not passed, it does seem that the ransom sort of works. Interestingly, the virus "developers" seem to be monitoring bulletin boards and fixing ransom "restore" bugs. I had to ask myself why, and the only answer is that if everyone agrees the restore does not work then no one would pay the ransom, and the software would just be more like "deleteware", and produce no money for the people who wrote and disseminate this.
Here is a great Sophos video of CryptoLocker in action (about 8 minutes).
Propagation: I have looked in lots of places for the means this is propagated. The best answer (and it may not be correct) is loading of Zbots, or Trojan viruses like voicemail.exe files sent to users. When they are launched, they download the CryptoLocker program in background and launch it. They target common files, like Word or Excel, Access, Powerpoint, PDF, JPG (photos, etc), Attempting to open one will generally cause an error that the file format is not recognized. When their evil work is done, they start the 72 hour clock. The decryption key is not on your machine, and that is what you need to decrypt your own files.
Removal of the virus:
The first thing to do if you suspect a problem is to disconnect the computer from the network to prevent it from encrypting all of your shared files. I personally would pull the plug on the computer, get a malware removal tool, start the machine in safe mode and start cleaning. Reddit has a bunch of threads that cover this in painful details, like this one: Reddit Guide to Bleeping CryptoLocker
It is important to note that removing the virus does NOT get your files back. They are still encrypted. Did I mention to backup your files?
Recommendations:
1. Make sure your backups are current, as this is the only way to recover from this virus.
2. Tell users that this is a "code Red" threat and not to open any suspicious attachments.
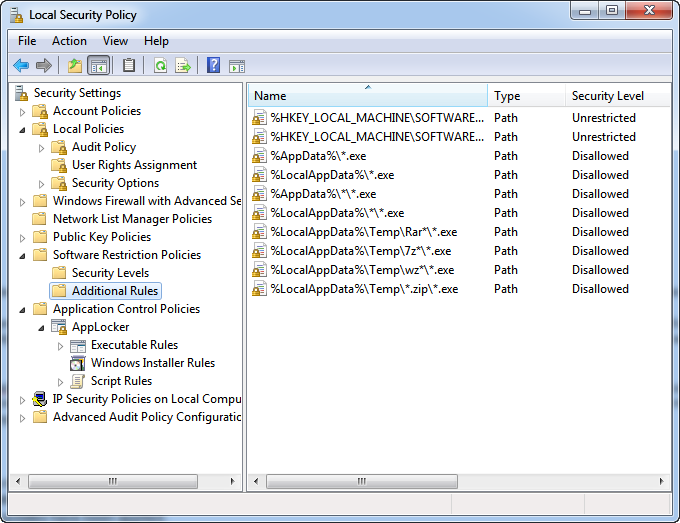
3. Add Local Security Policy to your PC.
( For domain admins, you can set this at the domain or site level using the Group Policy Object editor)
4. Make sure your anti-virus signatures are up to date and your all Windows Updates have been applied.
More Links:
As this post is a reference guide, I am posting this table of contents for Bleeping Computer in its entirety as I found it to be an excellent resource.
Bleeping Computer discussion Table of Contents
1. The purpose of this guide
2. What is CryptoLocker
3. What should you do when you discover your computer is infected with CryptoLocker
4. Is it possible to decrypt files encrypted by CryptoLocker?
5. Will paying the ransom actually decrypt your files?
6. Known Bitcoin Payment addresses for CryptoLocker
7. CryptoLocker and Network Shares
8. What to do if your anti-virus software deleted the infection files and you want to pay the ransom!
9. How to increase the time you have to pay the ransom
10. Is there a way to contact the virus author?
11. How to restore files encrypted by CryptoLocker using Shadow Volume Copies
12. How do you become infected with CryptoLocker
13. How to generate a list of files that have been encrypted
14. How to determine which computer is infected with CryptoLocker on a network
15. How to prevent your computer from becoming infected by CryptoLocker
16. How to allow specific applications to run when using Software Restriction Policies
17. How to be notified by email when a Software Restriction Policy is triggered
CryptoLocker Wikipedia page
Reddit Guide to Bleeping CryptoLocker
Read on only if you want to understand how to lock down your system, the following explains it in more detail. This was again based on these instructions on preventing the Zbot from loading in the first place
Manually Locking Down your System
Given that we are looking at viruses all the time in our main line of work blocking spam and viruses, I decided to manually lock down my main PC.
Below are my results.
To test this, I tried to launch Notepad.exe from a Zip file. Here is the error I expected:
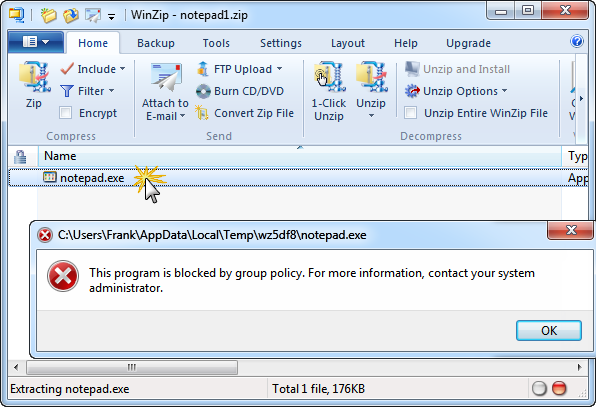
The same test with WinRAR:
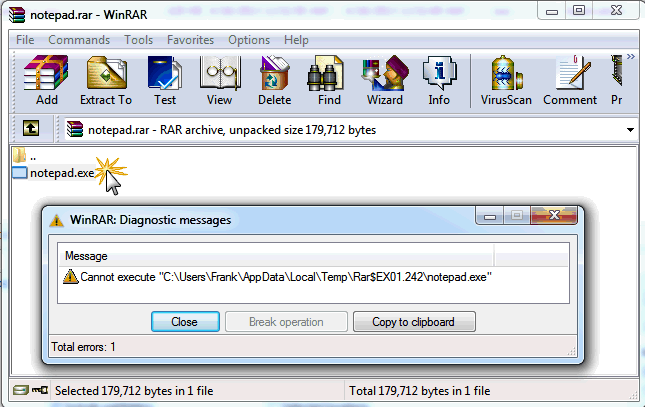
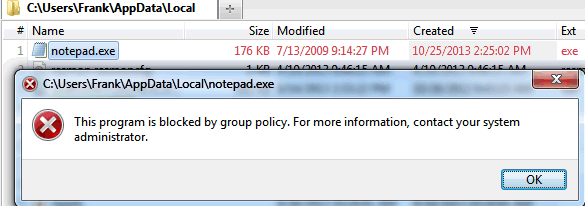
I ran a test by trying to run Notepad from the %appdata% folder and it was blocked:
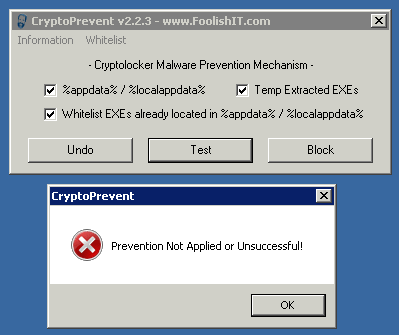
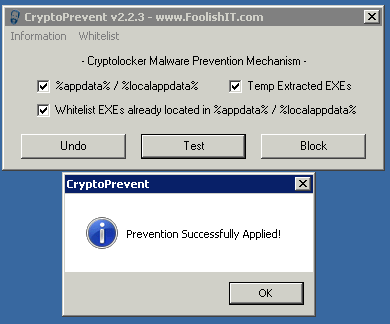
Using the CryptoPrevent Tool to Lock Down your System
This free tool from FoolishIT makes the same policy changes as above. CryptoPrevent artificially implants group policy objects into the registry in order to block certain executables in certain locations from running.
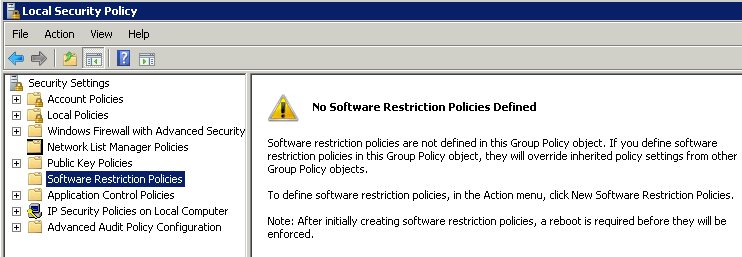
Note that because the group policy objects are artificially created, they will not display in the Group Policy Editor on a Professional version of Windows — but rest assured they are still there!
Installed and ran 'Test' first off
Then clicked 'Block'
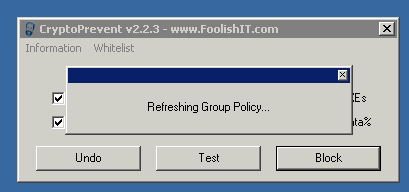
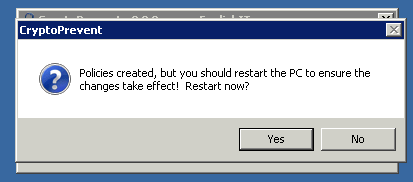
Restarted server and tested again
Note that because the group policy objects are artificially created, they will not display in the Group Policy Editor on a Professional version of Windows — but rest assured they are still there!
This is verified on my set-up: Policies cannot be seen.
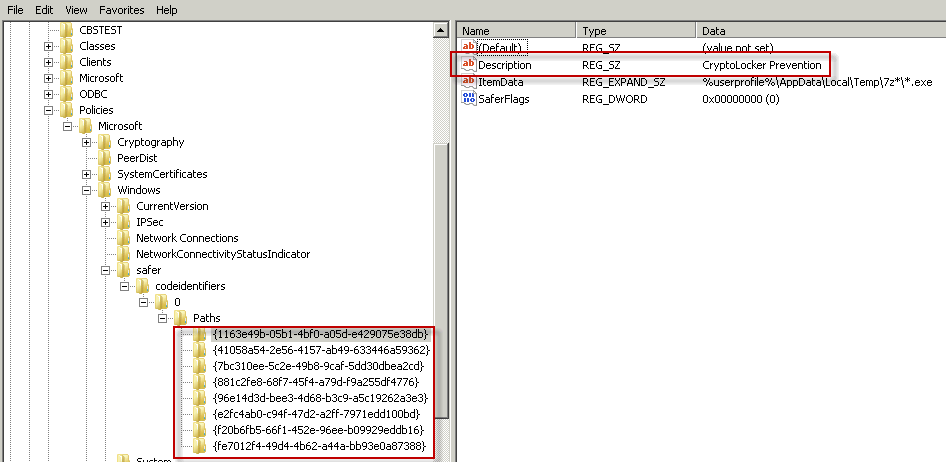
However - the keys are in the registry - HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\safer\codeidentifiers\0\Paths
Blog Tags
Cryptolocker